PAS detectors in the District of Utrecht should be given priority when issuing the nitrogen space from the Utrecht Nitrogen...
Dries Mertens was in Napoli on Wednesday. A visit that filled Neapolitans with nostalgia for the past. When he joined...
Intel is launching a Halo point onto the world: it's a prototype of a so-called nervous system, which works more...
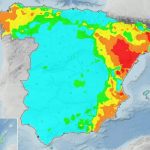
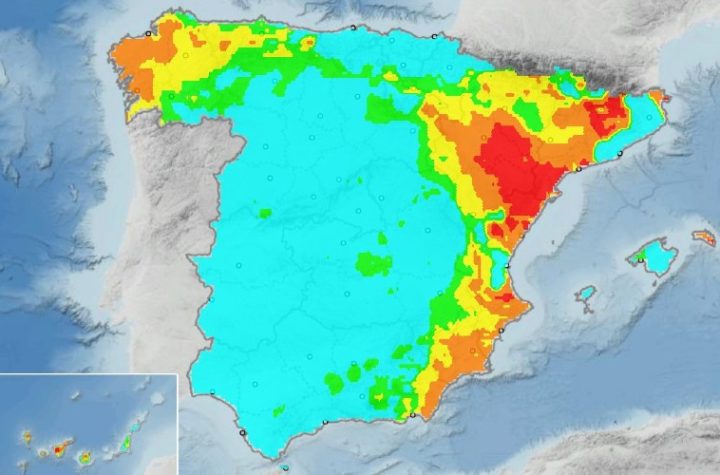
The Spanish Meteorological Service warned residents of the increasing risk of forest fires in several areas of the country. After...
“Yes, there is enough power,” says electric driving expert Blankaert. Although he makes a comment right away. “There will not...
The exception was not waived on the basis of the proposed expansion policy. This was stated by outgoing Agriculture Minister...
RSC Anderlecht beat Union SG 2-1. The Purple & White are now at the top of the Jupiler Pro League....
Chimpanzees and bonobos recognize old acquaintances, even if they haven't seen them in decades. This is clear from research conducted...
Just eat takeaway The focus is more on the United Kingdom and Ireland as orders elsewhere decline. In New Zealand,...
Proximus Mobile Vikings brand offers fixed 5Gb/s subscription for 90 euros per month – IT Pro – News
I'm calling total BS on this oneLegacy ADSL technology is simply asymmetric, which is what the A in ADSL stands...